5 Minutes, $44M: CoinDCX Hack Shows All the Signs of Lazarus Involvement
Inside the $44M CoinDCX Heist and Why India’s Exchanges Are Under Fire

India’s two largest exchanges- WazirX in 2024 and now CoinDCX in 2025, have been struck by devastating breaches. Both incidents happened on the same date, one year apart, following the same exploit pattern. Coincidence? Hardly.
Both were detected by Cyvers, and our analysis suggests this latest attack bears the hallmarks of North Korea’s Lazarus Group, one of the most aggressive state-sponsored hacker syndicates targeting centralized exchanges.
How the $44 Million CoinDCX Hack Unfolded
What makes this breach alarming isn’t just the $44.2 million (₹368 crore) drained from CoinDCX’s operational wallet—it’s the speed, precision, and cross-chain sophistication.
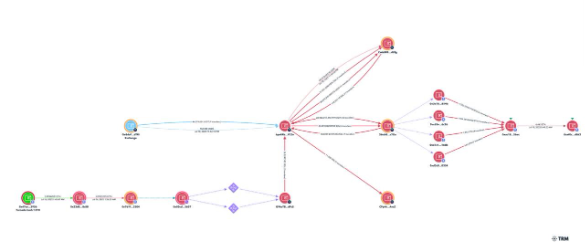
Pre-Attack Setup (July 16, 2025)
- 01:43 UTC – Funding sourced from Tornado Cash (Ethereum).
- 02:13 UTC – Funds funneled through FixedFloat, a rapid swap service.
- 02:17 UTC – Withdrawn to Polygon.
- 02:22 UTC – Bridged to Solana as SOL to cover gas fees.
Dry Run (July 18, 2025)
- 21:07 UTC – A 1 USDT “test” transaction is sent, signaling imminent execution.
The Breach (July 18, 2025)
- 22:09–22:14 UTC – In just five minutes, 44 million USDT is siphoned out in rapid-fire bursts (2M, 7M, 10M, 10M, 5M + 5M, and 5M).
- 23:43 UTC – Follow-up clean-up transactions move 102K USDC and 79K USDT.
Why Exchanges Are Struggling
CoinDCX’s leadership has assured customers that all losses will be covered from the exchange’s treasury and that user funds remain safe in cold storage. Trading and withdrawals continue to operate.
But the attack highlights a critical truth: legacy defenses can’t keep up with the speed and complexity of modern, state-sponsored hackers. In 2024 a 900% increase in losses at centralized exchanges over the prior year, driven largely by access-control breaches and private key compromises.
These attacks, often involving Lazarus Group, exploit exchange infrastructure, bypass traditional monitoring, and move assets across chains faster than manual detection can react.
How Cyvers Closes the Gap
Unlike reactive systems, Cyvers’ AI-powered Preemptive Threat Interceptor detects these patterns before damage is done. We do this by creating an off-chain simulation of the transaction, along with a validation of its maliciousness vs our threat intelligence engine. All this is done prior to transmitting the transaction to the blockchain – thus allowing the user to cancel or proceed with the transaction.
With preemptive playbooks, Cyvers can freeze compromised flows or alert exchanges before millions are drained.
CoinDCX. WazirX. Two years, two attacks, same date.

These aren’t coincidences, they’re warnings. If Lazarus is accelerating its focus on India’s largest exchanges, preemptive threat prevention isn’t optional. It’s the only line of defense.
Cyvers protects exchanges, custodians, and DeFi platforms from Lazarus-level threats. Don’t wait for the next headline- fortify your defenses now.
To schedule a call with the Cyvers team: https://calendly.com/d/cqjd-77h-r6x/cyvers-first-call?utm_medium=blog&utm_campaign=shiri
Next generation threat prevention
Identify patterns and anomalies across blockchains in real-time for proactive mitigation.




.webp)
.webp)
.webp)

.webp)
.webp)